No, They (NSA) Cannot Break SSL. They Don't Have To in [Market-Ticker]
No, They (NSA) Cannot Break SSL. They Don't Have To
Here you go folks -- and again, I get to use this sign:

By July 9, Lavabit still hadn’t defeated its security for the government, and prosecutors asked for a summons to be served for Lavabit, and founder Ladar Levison, to be held in contempt “for its disobedience and resistance to these lawful orders.”
A week later, prosecutors upped the ante and obtained the search warrant demanding “all information necessary to decrypt communications sent to or from the Lavabit email account [redacted] including encryption keys and SSL keys.”
There it is.
They wanted the SSL private key. Without it they can't decrypt ****. With it, for many (non-modern) browsers, they not only can decrypt messages in real time (by intercepting the setup "in the middle") they can retrospectively decrypt anything they stored previously as many browsers and other connecting devices do not use perfect forward secrecy.
What is that? It's a rather obscure bit of cryptographic tech-speak and has to do with how session keys are negotiated. Without it the secret key of the server can be used to retrospectively decrypt any traffic that was previously sent. This is much like how PGP operates -- if you get my Secret Key you can decrypt any message sent to me using the public key half no matter when it was sent.
Perfect Forward Secrecy uses the private key to negotiate a session key that is deliberately stored only in volatile memory and erased when the session's transmission ends. Since the actual secret key is not used other than in this negotiation and the details of that negotiation are intentionally destroyed when the session has ended compromise of the secret key does not help you decode previous transmissions.
It does, of course, allow you to intercept (by going "in the middle") any future transmissions.
Here's the rub -- most browsers do not implement PFS. Without it if "someone" (say, the NSA) has a copy of an encrypted transmission and later gets ahold of the secret key they can decrypt the transmission retrospectively.
So what did we learn from Lavabit?
- The spooks didn't "break" SSL; if they could have they would have as doing so would not require any help from or even knowledge of Lavabit. They instead tried to compel Lavabit to let them in the old-fashioned way, by demanding the key to the lock. Lavabit told them to go to Hell.
- The odds of any large entity having ever provided service to someone who has become the target of an investigation is effectively 100%.
- You therefore must assume that the secret keys that are in the possession of any of the large Certificate Authorities and any large business (such as Facebook, Microsoft, Google and similar) with customer-facing SSL (https) servers have been subpoenaed and are in the hands of the NSA and that in addition they have been gagged and unlike Lavabit are too pussified (or worse, bought) to refuse and/or disclose both the act and threat.
- You must assume that this means that the NSA can intercept any session to any mainstream eCommerce site or similar institution by "spoofing" the host in question (via a man-in-the-middle attack) since they have the secret key for all major CAs and thus can "replace" the certificate on the server end with one that is for the same site name even without the cooperation or even knowledge of the site involved. This, however, is detectable by you if you're paying attention as the server's key modulus will change -- but most people are not.
- You must assume that if the NSA subpoenas the secret key of an organization in general it will be provided and they will gag the organization from talking about it, allowing them to directly spoof the connection (even without the CA's involvement or without spoofing THEIR key!) If this has happened then your attempt to detect a key change as a means of alerting you to a possible compromise will fail. Your only defense against this compromise comes if the organization you are connecting does as Lavabit has done -- there is no other defense available to you.
- You must assume that this secret key, once divulged, can trivially be and thus will be used to decrypt not only the "target"'s transmissions but everyone else's, including yours even if you are not a target, for the purpose of "fishing."
- Worse, you must assume that nearly all browsers and other tools will not and did not ask for perfect forward secrecy, which means that any encrypted traffic you have ever sent to that site can be retrospectively decrypted once the secret key has been divulged even if you were not the original target -- or ever were a target -- of whatever investigation is now taking place.
- Therefore, if you want to "talk" to someone without this risk you must know that the other end (the server end) (1) set up their own CA and is the only party with the secret key for it, and (2) will not, and has not, divulged the SSL secret key to anyone. Finally, since anyone can be forced to divulge either or both in the future (e.g. by torture or legal threat and gag order) you must only use a client (web browser, email client, VPN client, etc) that implements Perfect Forward Secrecy so that if a compromise happens and you are made aware of it your previous conversations are not all instantly divulged at the same time. If you do not know all of these things, and in addition you cannot trust the other end to alert you via some means (e.g. by going dark!) if there is a compromise you must assume the compromise has occurred before your first transmission takes place.
Security? What's that? Oh by the way, if you're in a sensitive commercial environment (think securities, compliance in the financial realm, HIPPA, etc) this means that if (when) that secret key leaks from the government (Snowden anyone?) you're ****ed as that compromise extends to anyone who has that key and if PFS was not in use it is retrospective all the way back to first use if the traffic was logged.
The key point in all of this when it comes to "capability", however, remains as I have asserted:
Once again we have hard evidence that these NSA guys are not smarter than everyone else. They do not have the smartest guys in the room, and thus do not have a "braintrust" advantage sufficient to get what they want.
They're just plain old-fashioned jackbooted thugs who shove guns up people's noses to get what they're after, including spying on Americans, and we the people allow that crap to go on since we enable this **** through our Congress and payment of taxes.


One of my clients received an urgent notification to ditch all keys smaller than 2048 bits from their certificate provider this summer. I assume that change is mandated because some of the older keys were not compromised. We don't use the certificates for anything critical really. It prevents caching by proxy servers, which can sometimes break the apps and it reassures the customers.
My guess is that Obama has enabled most of this.
----------
--gh




It gets exponentially harder as the length goes up -- not linearly harder. If there are even minor weaknesses in the entropy source a 1024 bit key can be broken in a large (but possibly usable to an intruder) amount of time.
Good practice has been to run 2048 or 4096 bit keys now for the last few years. My CA key is 2048 bits, and my keys for private services are 4k bit while the Tickerforum https key is 2k. I recently replaced my older PGP key with a 4k bit key on the keyservers as well.
Fairly recent changes here have enabled PFS on connections to the site here (if your browser knows how) and all my local services; older OpenSSL versions did not know how to negotiate that. The big deal is really PFS as without that logged encrypted transmissions cannot be broken even if the private key is later compromised (that is, retrospective breaking of the cipher is an individual problem for each transmission rather than being made possible "en-masse" if the secret key is compromised.)
----------
All things have a season, and seasons change. -- MeI don't care if it makes sense -- only if it makes money. -- MeBank (n): See scam, fraud and theft.What part of "shall not be infringed" was unclear?
 Northwest Florida
Northwest Florida

KGB had nothing on these snakes!!!


However, the amount of effort required to break a 1024 bit key in this case would not yield the attacker anything of sufficient value to justify the effort.
BTW. This is off-topic but there is a hilarious post at hot-air, which was just put up less than 30 minutes ago.
http://hotair.com/greenroom/archives/201....
Quote:Sometimes, you just have to laugh. Yesterday, HHS Secretary Kathleen Sebelius made the MSM blitz by announcing the website, glitches and all, and the national call-in center, which is 1-800-318-2596. Now to make this work, you have to skip the 1, because on a phone keypad, no letters are assigned to the number 1. But spell out the rest, and this is what you get.
1-800-3(F) 8(U) 2(C) 5(K) 9(Y) 6(O).
----------
--gh




The notable exception is Windows XP (which doesn't support it at all) and older browsers that also don't support it.
SSL Labs calls our support for it "Robust" (if you can support it, we support it.)
One of my BIG complaints is that browsers DO NOT, as a rule, display whether forward security is enabled or not. In fact I don't think any of them do.
----------
All things have a season, and seasons change. -- MeI don't care if it makes sense -- only if it makes money. -- MeBank (n): See scam, fraud and theft.What part of "shall not be infringed" was unclear?
 Delaware
Delaware

I would think that with just 15 minutes a day of personal computer time on the system (yes I think there may be a threat at GS) and I would never have a bad trading day.
And that's the smart guy, the dumb ones would just try to sell the info to someone.
----------
You can't fix STUPID, but we've made it survivable.Quote:If the math says one thing and the law says something different, it will be the law that ends up changing
Charles Calomiris
 New York, by way of Montreal Canada.Online
New York, by way of Montreal Canada.Online

One of my BIG complaints is that browsers DO NOT, as a rule, display whether forward security is enabled or not. In fact I don't think any of them do.
Good opportunity for someone to build a plugin for the browsers.
----------




There's a disincentive for web site owners to enable it; it is a bit more computationally expensive. The difference isn't huge, but it's there.
----------
All things have a season, and seasons change. -- MeI don't care if it makes sense -- only if it makes money. -- MeBank (n): See scam, fraud and theft.What part of "shall not be infringed" was unclear?
 Saratoga Springs, New YorkOnline
Saratoga Springs, New YorkOnline

That's good enough for me yo.
----------
The most expensive thing you can have is a closed mind. -- Geoffrey FilburtEverything I write is my opinion and not to be considered proven fact. Nothing I write should be considered financial advice.
 Cary, NC
Cary, NC

Wouldn't it be great if the browser companies refused to have that little lock symbol appear after they handed all the keys over to the feds? That would have gotten everybody's attention. It would be in everyone's face and you would have mass protest over it. Man I wish those execs would grow a pair.
----------
There are no gun free zones where free men tread.
 Just North of Detroit
Just North of Detroit

What Little_eddie touched on here.I can run a hot dog stand or a dry cleaner or a lawn service and not worry about secrets.But who in their right mind would bet the farm to trust he had secrecy to run a BIG business today? Or try to patent (ha!)and produce a major consumer product? You have no guarantee some agency of the the government isn't going to steal it and hand it off to one of their favored business partners. All of which seem to be indistinguishable in morals and operating practice from the mafia.
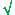


In an interesting work-around, Levison complied the next day by turning over the private SSL keys as an 11 page printout in 4-point type. The government, not unreasonably, called the printout illegible.
To make use of these keys, the FBI would have to manually input all 2,560 characters, and one incorrect keystroke in this laborious process would render the FBI collection system incapable of collecting decrypted data, prosecutors wrote.

----------
Death can take me if I can't be free. I am not like you, I'm a dying breed.
Online


http://news.netcraft.com/archives/2013/0....
Shows that all the sites listed in the prism program (except google) are not using PFS; which means one fism warrant to facebook, twitter and NSA can decrypt everything going to Facebook, twitter, etc...
Google appears to be the only property who might actually fighting them since they have been upgrading there keys; use PFS and have built into Chrome SSL certificate locking (this detects forged certs)...




Shows that all the sites listed in the prism program (except google) are not using PFS; which means one fism warrant to facebook, twitter and NSA can decrypt everything going to Facebook, twitter, etc...
Note that not using PFS means not only can they decrypt anything on a FORWARD basis but far more importantly, any SAVED ENCRYPTED SESSION GOING BACK TO THE ORIGINATION OF THE KEY can be decrypted retrospectively.----------
All things have a season, and seasons change. -- MeI don't care if it makes sense -- only if it makes money. -- MeBank (n): See scam, fraud and theft.What part of "shall not be infringed" was unclear?
 Nashville, TNOnline
Nashville, TNOnline

All these "conspiracy" charges, but nothing for an actual crime. "Conspiracy" bull**** when the occupying forces in DC can't come up with anything better.
----------
- Every normal man must be tempted at times to spit on his hands, hoist the black flag, and begin to slit throats. H. L. Mencken- These are the times that try men's souls. - T. Paine
 Around the WorldOnline
Around the WorldOnline

How about a PKI system like DOD CAC? that way you know what kind of connection you have, even if the modern browsers use forward security, but you don't know what type of connection since they don't display it, and apparently there is no way to turn that indication on.
Online


A week later, prosecutors upped the ante and obtained the search warrant...
How ironic that the "prosecutors" wagging their beetlebrows over what Snowden did are serving a treasonous piece-of-****-in-chief who delivered weaponry to the enemies of the United States.
The "prosecutors" are no different than Roland Freisler. I spit on them.
----------
====If it's true that "assault weapons" are "weapons of war" and don't belong on the streets of America, why do the police need them? Who are the police at war with?