Microsoft Darkens 4MM Sites in Malware Fight






Millions of Web sites were shuttered Monday morning after Microsoft executed a legal sneak attack against a malware network thought to be responsible for more than 7.4 million infections of Windows PCs worldwide.
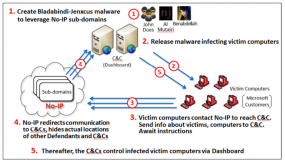
A diagram showing how crooks abused no-ip.com’s services to control malware networks. Source: Microsoft.
In its latest bid to harness the power of the U.S. legal system to combat malicious software and cybercrooks, Microsoft convinced a Nevada court to grant the software giant authority over nearly two dozen domains belonging to no-ip.com, a company that provides dynamic domain name services.
Dynamic DNS services are used to map domain names to numeric Internet address that may change frequently. Typically, the biggest users of dynamic DNS services are home Internet users who wish to have a domain name that will always point back to their home computer, no matter how many times their ISP changes the numeric Internet address assigned to that computer.
In this case, however, the attackers responsible for leveraging these two malware families — remote-access Trojans known as “njrat” and “njw0rm” — were using no-ip.com’s services to guarantee that PCs infected with this malware would always be able to reach the Internet servers that the attackers were using to control them.
Microsoft told the court that miscreants who were using these two malware strains were leveraging more than 18,400 hostnames that belonged to no-ip.com. On June 26, the court granted Microsoft the authority to temporarily seize control over 23 domains owned by no-ip.com — essentially all of the domains that power no-ip.com’s free dynamic DNS services.
Microsoft was supposed to filter out the traffic flowing to and from those 18,400+ hostnames, and allow the remaining, harmless traffic to flow through to its rightful destination. But according to no-ip.com marketing manager Natalie Goguen, that’s not at all what happened.
“They made comments that they’d only taken down bad hostnames and were supposedly redirecting all good traffic through to users, but it’s not happening, and they’re not able to handle our traffic volumes,” Goguen said. “Many legitimate users that use our services have been down all day.”
Goguen said while Microsoft claimed that there were more than 18,000 malicious hostnames involved, no-ip.com could only find a little more than 2,000 from that list that were still active as of Monday morning. Meanwhile, some four million hostnames remain offline, with customer support requests piling up.
“So, to go after 2,000 or so bad sites, [Microsoft] has taken down four million,” Goguen said.
Microsoft told the Nevada court that despite numerous reports released by Internet security firms over the past year about large volumes of malicious activity emanating from no-ip.com’s service, the company “consistently failed to take sufficient steps to correct, remedy, or prevent the abuse and to keep its domains free from malicious activity.”
But according to Goguen, the first time Microsoft brought its concerns to no-ip.com was at 7 a.m. on June 30, when the company’s CEO received a knock on the door of his family home and was served with a copy of the court order granting Microsoft authority over the 23 no-ip.com domains.
“We work with law enforcement all the time, and our abuse department responds to abuse requests within 24 hours,” Goguen said. “It’s pretty sad that Microsoft had to take such extreme measures to go about this.”
Goguen isn’t the only one who believes Microsoft swatted a fly with the equivalent of an atom bomb. Some of Microsoft’s previous legal sneak attacks targeted “bulletproof” hosting providers — those that promise to keep sketchy (and high-paying) customers online despite pressure from security firms and law enforcement. But according to Dmitri Alperovitch, co-founder of security firm CrowdStrike, treating no-ip.com like one of these shady providers is a mistake.
“They have always been very responsive to security researchers and law enforcement,” Alperovitch said of no-ip.com. “I do not consider them a bullet-proof or abuse-proof host.”
Meanwhile, Goguen said no-ip.com is considering its legal options for responding to the outage and to Microsoft’s allegations that the company somehow turns a blind eye to abuse complaints.
“We’re speaking with our lawyers about this, but right now we’re doing everything we can to fix this, and we need our users to understand that.”
In tandem with the action against no-ip.com, Microsoft also named and accused two men — software developers thought to reside in Kuwait and Algeria — of authoring and selling the njrat and njw0rm.
The complaint against no-ip, the accused malware authors, and the rest of Microsoft’s various legal filings in this case are available at this link.
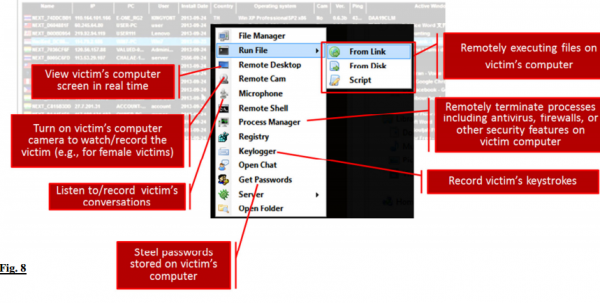
Capabilities of the “njrat” malware, as described in Microsoft’s court filing.
Tags: CrowdStrike, Dmitri Alperovitch, microsoft, Natalie Gogun, njrat, njw0rm, no-ip.com, no-ip.com outage
This entry was posted on Tuesday, July 1st, 2014 at 1:02 am and is filed under A Little Sunshine. You can follow any comments to this entry through the RSS 2.0 feed. You can skip to the end and leave a comment. Pinging is currently not allowed.
