FAUXTRIBUTION? | Krypt3ia
Well here we are… It’s the beginning of the cyber wars my friends. POTUS came out on stage and said that we would have a “proportionate response” to the hacking of Sony and that in fact the US believes that it was in fact Kim Jong Un who was behind this whole thing. Yup, time to muster the cyber troops and attack their infrastructure!
*chortle*
So yeah, let’s take a step back here and ponder the FBI statement today on colonel mustard in the study with the laptop before we go PEW PEW PEW ok?
FBI Statement:
Today, the FBI would like to provide an update on the status of our investigation into the cyber attack targeting Sony Pictures Entertainment (SPE). In late November, SPE confirmed that it was the victim of a cyber attack that destroyed systems and stole large quantities of personal and commercial data. A group calling itself the “Guardians of Peace” claimed responsibility for the attack and subsequently issued threats against SPE, its employees, and theaters that distribute its movies.
The FBI has determined that the intrusion into SPE’s network consisted of the deployment of destructive malware and the theft of proprietary information as well as employees’ personally identifiable information and confidential communications. The attacks also rendered thousands of SPE’s computers inoperable, forced SPE to take its entire computer network offline, and significantly disrupted the company’s business operations.
After discovering the intrusion into its network, SPE requested the FBI’s assistance. Since then, the FBI has been working closely with the company throughout the investigation. Sony has been a great partner in the investigation, and continues to work closely with the FBI. Sony reported this incident within hours, which is what the FBI hopes all companies will do when facing a cyber attack. Sony’s quick reporting facilitated the investigators’ ability to do their jobs, and ultimately to identify the source of these attacks.
As a result of our investigation, and in close collaboration with other U.S. government departments and agencies, the FBI now has enough information to conclude that the North Korean government is responsible for these actions. While the need to protect sensitive sources and methods precludes us from sharing all of this information, our conclusion is based, in part, on the following:
- Technical analysis of the data deletion malware used in this attack revealed links to other malware that the FBI knows North Korean actors previously developed. For example, there were similarities in specific lines of code, encryption algorithms, data deletion methods, and compromised networks.
- The FBI also observed significant overlap between the infrastructure used in this attack and other malicious cyber activity the U.S. government has previously linked directly to North Korea. For example, the FBI discovered that several Internet protocol (IP) addresses associated with known North Korean infrastructure communicated with IP addresses that were hardcoded into the data deletion malware used in this attack.
- Separately, the tools used in the SPE attack have similarities to a cyber attack in March of last year against South Korean banks and media outlets, which was carried out by North Korea.
We are deeply concerned about the destructive nature of this attack on a private sector entity and the ordinary citizens who worked there. Further, North Korea’s attack on SPE reaffirms that cyber threats pose one of the gravest national security dangers to the United States. Though the FBI has seen a wide variety and increasing number of cyber intrusions, the destructive nature of this attack, coupled with its coercive nature, sets it apart. North Korea’s actions were intended to inflict significant harm on a U.S. business and suppress the right of American citizens to express themselves. Such acts of intimidation fall outside the bounds of acceptable state behavior. The FBI takes seriously any attempt—whether through cyber-enabled means, threats of violence, or otherwise—to undermine the economic and social prosperity of our citizens.
The FBI stands ready to assist any U.S. company that is the victim of a destructive cyber attack or breach of confidential business information. Further, the FBI will continue to work closely with multiple departments and agencies as well as with domestic, foreign, and private sector partners who have played a critical role in our ability to trace this and other cyber threats to their source. Working together, the FBI will identify, pursue, and impose costs and consequences on individuals, groups, or nation states who use cyber means to threaten the United States or U.S. interests.
Parsing the language:
- Technical analysis of the data deletion malware used in this attack revealed links to other malware that the FBI knows North Korean actors previously developed. For example, there were similarities in specific lines of code, encryption algorithms, data deletion methods, and compromised networks.
- The FBI also observed significant overlap between the infrastructure used in this attack and other malicious cyber activity the U.S. government has previously linked directly to North Korea. For example, the FBI discovered that several Internet protocol (IP) addresses associated with known North Korean infrastructure communicated with IP addresses that were hardcoded into the data deletion malware used in this attack.
- Separately, the tools used in the SPE attack have similarities to a cyber attack in March of last year against South Korean banks and media outlets, which was carried out by North Korea.
The language of this report is loose and very much like an FBI statement would be when they are not so sure. Remember that the FBI did not originally link all of this to DPRK. Now though, with the same data as we all had before they are definitively tentatively saying “It’s DPRK” which makes people like me mental. So let’s look at these IP’s that were hard coded into the malware and take the idea to task that they are assets that ONLY the DPRK could use or has used and how that very idea has so much cognitive dissonance where “evidence” is concerned. Especially evidence where a nation state is going to “respond proportionally” to another for actions they claim they perpetrated.
The key here is to pay attention to the GEO-IP stuff they are using:
A summary of the C2 IP addresses:
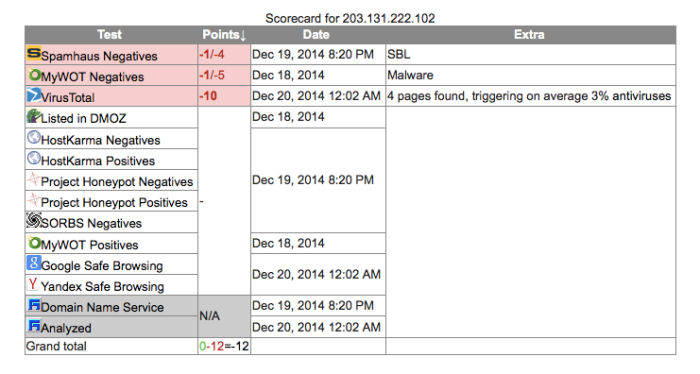
| 203.131.222.102 | Thailand | 8080 | Diskpartmg16.exeigfxtrayex.exeigfxtpers.exe |
| 217.96.33.164 | Poland | 8000 | Diskpartmg16.exeigfxtrayex.exe |
| 88.53.215.64 | Italy | 8000 | Diskpartmg16.exeigfxtrayex.exe |
| 200.87.126.116 | Bolivia | 8000 | File 7 |
| 58.185.154.99 | Singapore | 8080 | File 7 |
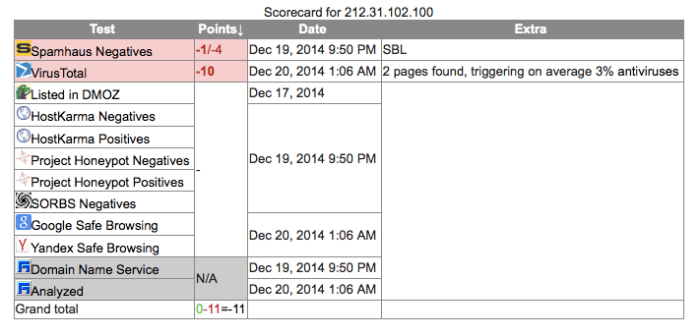
| 212.31.102.100 | Cypress | 8080 | File 7 |
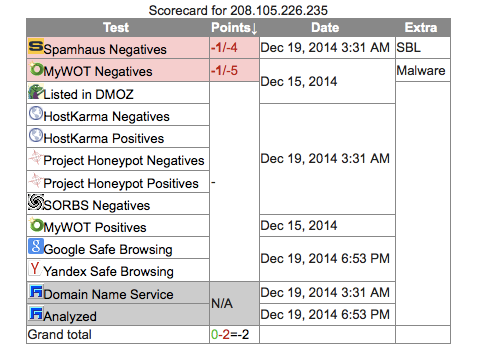
| 208.105.226.235 | United States | – | igfxtpers.exe |
See now all of these IP’s could be used by just about anyone. They are not in country at the DPRK and they are not on Chinese soil either. In fact here is the dope on each one:
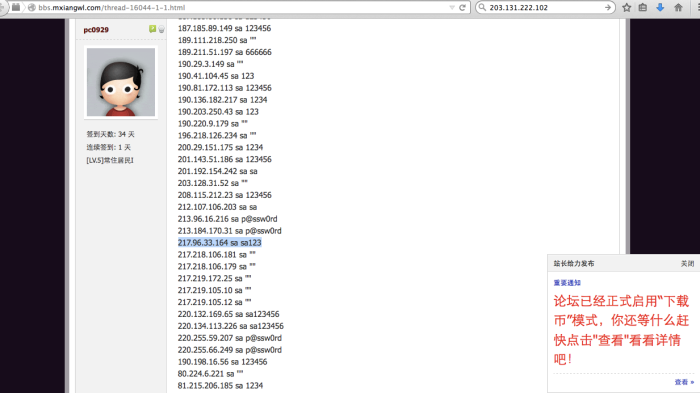
Thailand: 203.131.222.102: Thailand port 8080 is a proxy:
| 203.131.222.102 | - | 203.131.222.102 | 203.131.222.102 | 203.131.222.0/23 Proxy-registered route object THAMMASAT Thammasat University 2 Phrachan Road, Phranakorn, Bangkok 10200, Thailand | AS37992 THAMMASAT-BORDER-AS Thammasat University | Thailand |
It has also been seen as a very dirty player in SPAM and other nefarious actions.. Not just DPRK/CN APT Activities
 So really, this one could be used by anyone and everyone.
So really, this one could be used by anyone and everyone.
Poland: 217.96.33.164 8080:
| 217.96.33.164 | - | 217.96.33.164 | 217.96.33.164 | 217.96.0.0/16 TPNET INTER-PARTS INTER-PARTS IMPORT EKSPORT WALDEMAR BACLAWSKI UL. JARZEBINOWA 4 11-034 STAWIGUDA | AS5617 TPNET Orange Polska Spolka Akcyjna | Olsztyn, Poland |
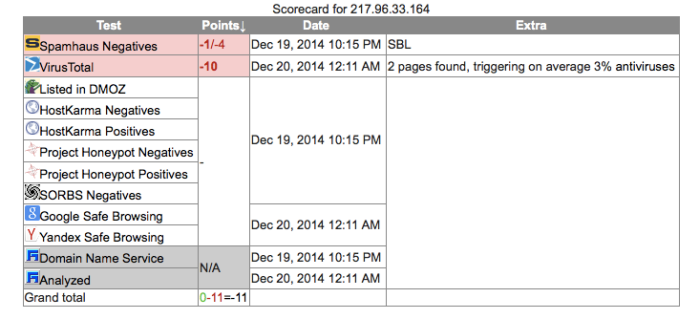 Poland too is known to be dirty and used for SPAM and malware C&C’s as well. Many different groups are using this and it too is a proxy. So once again, this does not prove out solidly that this is DPRK. It could in fact be anyone who is in the know about it’s being there and use. Many of these addresses are on sites all over the web for use in this and other capacities.
Poland too is known to be dirty and used for SPAM and malware C&C’s as well. Many different groups are using this and it too is a proxy. So once again, this does not prove out solidly that this is DPRK. It could in fact be anyone who is in the know about it’s being there and use. Many of these addresses are on sites all over the web for use in this and other capacities.
In fact here is a site that has the password to the system (Chinese)
Italy 88.53.215.64 8000
| 88.53.215.64 | - | 88.53.215.64 | 88.53.215.64 | 88-53-215-64.WDSL.NEOMEDIA.IT | 88.52.0.0/15 INTERBUSINESS IT-INTERBUSINESS-20050930 Telecom Italia S.p.a. | AS3269 ASN-IBSNAZ Telecom Italia S.p.a. | Italy |
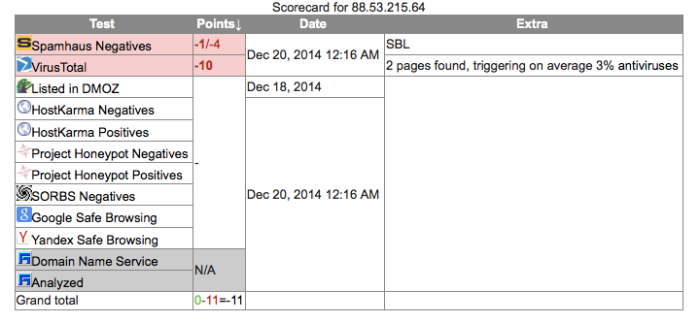 Once again, Italy has the same issue. It is a known dirty address/system and has been used for SPAM and Malware C&C’s before. This does not mean that it is in fact solely under the control of DPRK.
Once again, Italy has the same issue. It is a known dirty address/system and has been used for SPAM and Malware C&C’s before. This does not mean that it is in fact solely under the control of DPRK.
Site listing the proxy as available and the qualities of the anonymity
Here’s another listing: http://dogdev.net/Proxy/IT
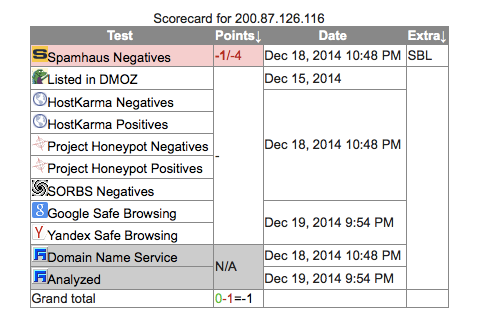
Bolivia 200.87.126.116 8000
| 200.87.126.116 | - | 200.87.126.116 | 200.87.126.116 | 200.87.112.0/20200.87.126.0/24 This is a DiViNetworks customer route-object which is being exported under this origin AS6568 (origin AS). This route object was created because no existing route object with the same origin was found. Please contact support@divinetworks.com if you have any questions regarding this object. BO-ESEN-LACNIC Entel S.A. – EntelNet | AS6568 ENTEL-SA-BOLIVIA ENTEL S.A. BOLIVIA | La Paz, Bolivia |
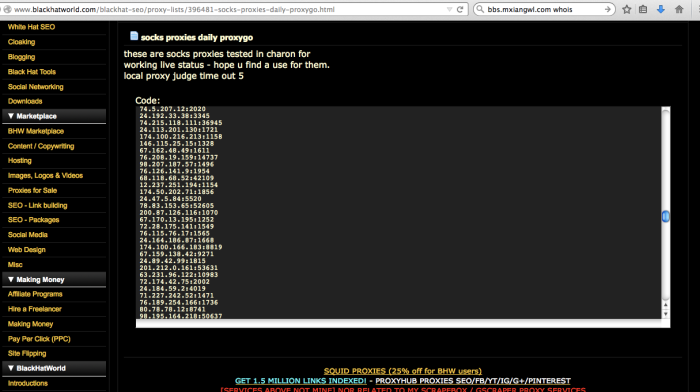
Here’s a listing from 2012 on the Bolivian proxy (blackhat forum)
Another listing: http://www.vipsocks24.com/2012/01/20-01-12-l1l2-anonymous-proxies-list.html
Starting Nmap 6.47 ( http://nmap.org ) at 2014-12-20 05:15 ESTNmap scan report for 200.87.126.116Host is up (0.17s latency).Not shown: 92 closed portsPORT STATE SERVICE VERSION80/tcp open http Apache httpd 2.2.3 ((Win32))135/tcp open msrpc Microsoft Windows RPC139/tcp filtered netbios-ssn445/tcp filtered microsoft-ds1720/tcp filtered H.323/Q.9315800/tcp open vnc-http RealVNC 4.0 (resolution: 400×250; VNC TCP port: 5900)(remote auth bypass)5900/tcp open vnc RealVNC Personal (protocol 4.0)10000/tcp open http GeoVision GeoHttpServer for webcams
Singapore 58.185.154.99 8080
| 58.185.154.99 | - | 58.185.154.99 | 58.185.154.99 | 58.185.128.0/17 Singapore Telecommunications Ltd SINGNET-SG SingNet Pte Ltd 2 Stirling Road #03-00 Queenstown Exchange Singapore 148943 | AS3758 SINGNET SINGNET | Singapore, Singapore |
Singapore Proxy on offer online
TEXT
Cyprus 212.31.102.100 8080
| 212.31.102.100 | - | 212.31.102.100 | 212.31.102.100 | NB5-100.STATIC.CYTANET.COM.CY | 212.31.96.0/20212.31.100.0/22 Proxy-registered route object CYTANET PROVIDER Local Registry | AS6866 CYTA-NETWORK Cyprus Telecommunications A | Cyprus |
TEXT
USA 208.105.226.235 (no port listed)
| 208.105.226.235 | - | 208.105.226.235 | 208.105.226.235 | RRCS-208-105-226-235.NYS.BIZ.RR.COM | 208.105.128.0/17 RR-Route RCNY | AS11351 RoadRunner RR-Binghamton-Rochester | Syracuse, United States |
Starting Nmap 6.47 ( http://nmap.org ) at 2014-12-19 21:13 ESTNmap scan report for rrcs-208-105-226-235.nys.biz.rr.com (208.105.226.235)Host is up (0.070s latency).Not shown: 94 filtered portsPORT STATE SERVICE135/tcp open msrpc443/tcp open https3128/tcp closed squid-http