Intel Security Risk Is Much Worse Than Management Commentary Indicates - Intel Corporation (NASDAQ:INTC) | Seeking Alpha
As security concerns about its processors mounted, Intel (INTC) responded to the developments and followed it up with a conference call further alleviate investor concerns.
As we demonstrate below, Intel’s narrative on the subject is not fully credible.
To begin with, investors need to familiarize themselves with the problem. The security issue appears to have been first notified to Intel on 6/1/2017 by Google Project Zero team. (The Google (GOOG) (GOOGL) link may be hard to understand and non-technically inclined investors may find the explanation of Meltdown and Spectre much more comprehensible).
In short, the problem is about malicious code having access to unauthorized information on the system. Information such as passwords, personal data, and critical documents. The security concerns are severe. Per standard industry practices, Intel, and several industry players including Advanced Micro Devices (AMD), ARM, Microsoft (MSFT), several software and security companies, have been working on understanding the scope of the problem and identifying fixes to mitigate the problem.
The status of affairs now is that Meltdown, something that seems to be impacting mainly Intel processors, is an immediate challenge that needs to be mitigated. Spectre, on the other hand, is a tougher exploit that affects all modern microprocessors but is not an immediate concern. Spectre is being seen as a likely long-term problem for the industry.
Information that has become available over the last few days indicates that some of the fixes for Meltdown require extensive changes to operating systems such as Linux and Windows and have severe performance implications. While some consumer benchmarks have barely shown any deterioration, some database and cloud-related benchmarks have shown 5% to 30% performance impact. Some benchmarks have shown even more severe performance degradation close to 50%.
AMD is on the record that the Meltdown-related fixes do not apply to its processor architecture and there is no need for performance-crippling patches for its products.
With this backdrop, how does Intel address the issue?
Abysmally.
For example, Intel says in its press release and subsequent presentation that:
“Intel believes these exploits do not have the potential to corrupt, modify or delete data.”
Note that the security issue is not about corrupting, modifying, or deleting data. It is about unauthorized access to critical data. Intel is certainly not addressing the root cause of concern here.
Intel may also not be telling the whole truth when it says:
“Recent reports that these exploits are caused by a “bug” or a “flaw” and are unique to Intel products are incorrect. Based on the analysis to date, many types of computing devices — with many different vendors’ processors and operating systems — are susceptible to these exploits.”
While this is technically true, the real problem at hand, severe performance degradation, seems to not apply to AMD but only to Intel.
Intel goes a step further and throws mud in the discussion by saying:
“Intel is committed to product and customer security and is working closely with many other technology companies, including AMD, ARM Holdings and several operating system vendors, to develop an industry-wide approach to resolve this issue promptly and constructively.”
This sentence seems to implicate AMD and ARM without quite saying that they too may have problems. Intel continues the obfuscation with the following statement:
“Intel has begun providing software and firmware updates to mitigate these exploits. Contrary to some reports, any performance impacts are workload-dependent, and, for the average computer user, should not be significant and will be mitigated over time.”
While it is true that Intel is providing software and firmware, as they should, saying that performance impact to the “average computer user” is insignificant is an incomplete statement. The security issues, especially from Meltdown, appear to be big challenges for not “average computer users” but for server and data center deployments.
Intel caps off its response with what we deem to be an incredulous statement:
“Intel believes its products are the most secure in the world and that, with the support of its partners, the current solutions to this issue provide the best possible security for its customers.”
How Intel can claim that its products are most secure when its products have found to be lacking is beyond us.
Intel’s dancing around the issue and evading specifics got worse in the subsequent conference call.
During the call, Intel acknowledged that it has seen no degradation in some applications and up to 30% degradation in some applications. Intel did not want to get into details on the impact on desktop or laptop PC users and server or cloud users but there is abundant information in the public domain that indicates that the server and cloud applications are likely the most impacted.
Intel claimed that these security issues have no financial impact on Intel. We are extremely skeptical about this claim because the performance impact of the fixes can be high. A hypothetical 10% performance hit from the bug fixes would mean that server cloud customers would have to add 10% more in CPU resources to mitigate the performance problem. This can be a big cost hit for today’s data centers. It is difficult to see server and cloud customers giving Intel a free pass on this one.
Considering the scope of the problem and given that all Intel processors on the field are impacted, and AMD processors are not impacted, it is easy to visualize multi-billion recall situations for Intel.
Intel also skipped answering questions about competitive impact. With AMD's EPYC chip already being a strong server contender even before this security issue surfaced, it is easy to see that Intel will be in a worse competitive position. With some benchmarks seeing 30% impact, it will become much easier for AMD to win server and cloud sockets. And, AMD will have a stronger security story to the boot.
What is even worse is that Intel now has the need to delay future product releases to incorporate the fixes for this security problem. We expect a minimum 6-month delay to allow for design and validation of most future product releases (especially the Xeon family). This will make Intel’s product roadmap that much less competitive with AMD.
AMD has already come up with a counter to Intel since Intel’s initial claims which indicate that AMD products do not have the same susceptibilities.
In our view, the security problem is a much bigger problem than Intel is acknowledging, and Intel investors will be in for a very rough ride for the next couple of years. While Intel may not have much of a problem on the consumer side from this security issue, in our view, Intel’s data center business is at a serious risk.
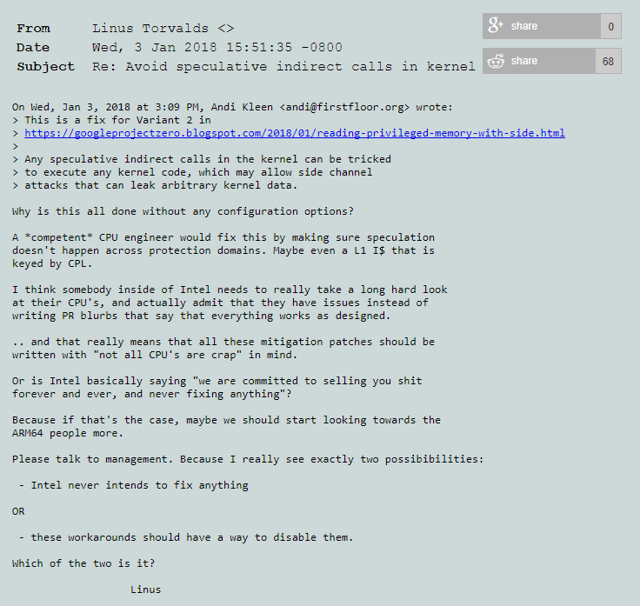
Furthermore, the PR effort is in such a poor form, it makes Intel looks bad. Note what Linus Torvalds, creator of Linux, has to say on the subject (image below)
Summary
In spite of Intel's claims otherwise, this security problem is a big deal and this also piles up on Intel’s deteriorating competitive position.
Given that Intel’s products have the problem and AMD products do not, in effect, AMD solutions are incrementally better by up to 30% and have superior security in our opinion. This makes Intel’s server and data center prospects very cloudy.
With a whole host of product, process, and security-related problems, the time has now come for investors to sell Intel short.
Our view of Intel: Sell Short
For timely, cutting-edge insights, analysis and investing ideas of solar, battery, autonomous vehicles, and other emerging technology stocks, check outBeyond the Hype. This Marketplace service gives you early access to my best investing ideas, along with event driven and arbitrage opportunities when they are most edgy and actionable. If you want expert advice on seeing through the hype, separating fact from fiction, avoiding investing landmines in emerging technologies, and an opportunity to participate in a vibrant and intellectually stimulating real-time chat room with other high-caliber, like-minded investors, consider subscribing to Beyond the Hype today.
Disclosure: I am/we are long AMD.
I wrote this article myself, and it expresses my own opinions. I am not receiving compensation for it (other than from Seeking Alpha). I have no business relationship with any company whose stock is mentioned in this article.
Additional disclosure: Long INTC puts Author’s investment philosophy is long only and author does not short. Shorting is a sophisticated investment strategy that requires superior investment skills and must be avoided by all but experienced investors with the appropriate skill and wherewithal.