How a “location API” allows cops to figure out where we all are in real-time | Ars Technica
Nowhere to run to, nowhere to hide —
"Securus takes no steps to verify that uploaded documents in fact provide authorization…"
Cyrus Farivar - May 12, 2018 12:30 pm UTC

Jaap Arriens/NurPhoto via Getty Images
The digital privacy world was rocked late Thursday evening when The New York Times reported on Securus, a prison telecom company that has a service enabling law enforcement officers to locate most American cell phones within seconds. The company does this via a basic Web interface leveraging a location API—creating a way to effectively access a massive real-time database of cell-site records.
Securus’ location ability relies on other data brokers and location aggregators that obtain that information directly from mobile providers, usually for the purposes of providing some commercial service like an opt-in product discount triggered by being near a certain location. ("You’re near a Carl’s Jr.! Stop in now for a free order of fries with purchase!")
The Texas-based Securus reportedly gets its data from 3CInteractive, which in turn buys data from LocationSmart. Ars reached 3CInteractive's general counsel, Scott Elk, who referred us to a spokesperson. The spokesperson did not immediately respond to our query. But currently, anyone can get a sense of the power of a location API by trying out a demo from LocationSmart itself.
Currently, the Supreme Court is set to rule on the case of Carpenter v. United States, which asks whether police can obtain over 120 days worth of cell-site location information of a criminal suspect without a warrant. In that case, as is common in many investigations, law enforcement presented a cell provider with a court order to obtain such historical data. But the ability to obtain real-time location data that Securus reportedly offers skips that entire process, and it's potentially far more invasive.
Securus’ location service as used by law enforcement is also currently being scrutinized. The service is at the heart of an ongoing federal prosecution of a former Missouri sheriff’s deputy who allegedly used it at least 11 times against a judge and other law enforcement officers.
On Friday, Sen. Ron Wyden (D-Oregon) submitted formal letters to AT&T and also to the Federal Communications Commission demanding detailed answers regarding these Securus revelations.
"To access this private data, correctional officers simply visit Securus’ Web portal, enter any US wireless phone number, and then upload a document purporting to be an official document giving permission to obtain real-time location data," Wyden wrote.
Blake Reid, a law professor at the University of Colorado, told Ars that he was unfamiliar with services like this that allow police to obtain, in real-time, location information for nearly any number with little scrutiny.
"That’s certainly pretty unprecedented," he said. "This isn't how it's supposed to work for law enforcement to get location data—they’re supposed to get it from the phone companies."
Securus did not immediately respond to Ars’ request for comment, but a spokesman told the Times in a statement that "responsibility of ensuring the legal adequacy…lies with our law enforcement customers and their counsel." For its part, Securus' "ensuring" seems to consist of nothing more than a check box on a website.
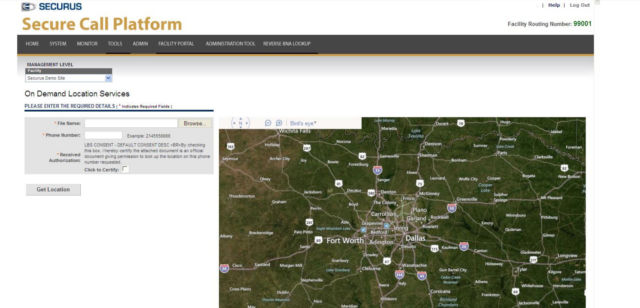
Securus
"Top officials at Securus confirmed to my office that Securus takes no steps to verify that uploaded documents in fact provide authorization for real-time surveillance, or conduct any review of surveillance requests," Wyden continued. "Securus claimed, incorrectly, that correctional facilities, not Securus, must ensure that correctional officers don’t misuse the Web portal."