FBI Takes Control of APT28's VPNFilter Botnet

The US Federal Bureau of Investigation (FBI) has obtained court orders and has taken control of the command and control servers of a massive botnet of over 500,000 devices, known as the VPNFilter botnet.
The existence of this massive threat came to light yesterday when Cisco Talos published a report about VPNFilter infecting over 500,000 routers and NAS devices across the world.
FBI: APT28 is behind VPNFilter
Cisco said the botnet appeared to be preparing for an attack on Ukraine, as the botnet's operators were working hard to infect as many devices as possible within the country.
The Ukrainian Secret Service believed the attack was supposed to take place on Saturday when the Ukrainian capital of Kiev is hosting the UEFA Champions League soccer final.
The FBI confirmed that the botnet has been created and was under the control of a famous Russian cyber-espionage unit known under different names, such as APT28, Sednit, Fancy Bear, Pawn Storm, Sofacy, Grizzly Steppe, STRONTIUM, Tsar Team, and others.
A report authored by the Estonian Foreign Intelligence Service claims APT28 is a unit of the Russian Military's Main Intelligence Directorate (abbreviated GRU).
This group has been behind several cyber-attacks aimed at Ukraine in the past, such as the NotPetya ransomware outbreak, and the BlackEnergy attacks on Ukraine's power grid in 2015 and 2016.
FBI seizes control of VPNFilter's C&C domain
Security experts deemed the VPFilter botnet incredibly dangerous, not only because it was the work of a nation-state cyber group with nefarious reasons, but because it also included functions to intercept network traffic, search for SCADA equipment, and wipe firmware to temporarily brick devices.
With such powerful capabilities, and with devices infected all over the world, US authorities stepped in to prevent further damage from this threat.
Hours after the publication of the Cisco report, the FBI had obtained a court order based on a submitted affidavit to take control over the domain toknowall.com, the URL where VPNFilter bots would connect to get their commands and additional modules.
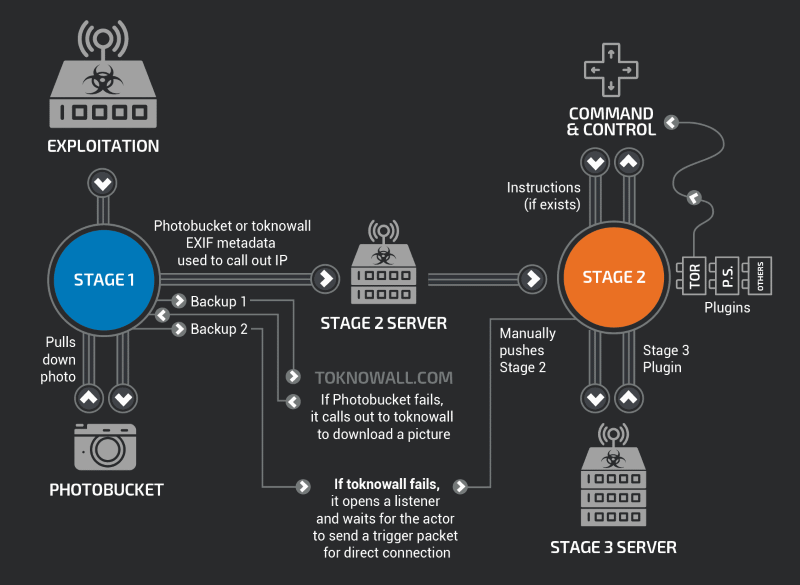
FBI asks users to reset devices to get a list of victims
With the domain firmly in its grasp, the FBI is now asking users across the world who own affected routers and NAS devices to reset their equipment.
The reasoning, according to the FBI, is to make these devices reconnect to the command and control server, giving the FBI a full insight into the botnet's real size.
The FBI plans to use this knowledge to create a list of vulnerable devices and notify ISPs, private and public sector partners that can deal with the infected devices.
Owners of the following types of devices are vulnerable to the VPNFilter malware, and should reboot their devices, based on the FBI's advice:
Linksys E1200
Linksys E2500
Linksys WRVS4400N
Mikrotik RouterOS for Cloud Core Routers: Versions 1016, 1036, and 1072
Netgear DGN2200
Netgear R6400
Netgear R7000
Netgear R8000
Netgear WNR1000
Netgear WNR2000
QNAP TS251
QNAP TS439 Pro
Other QNAP NAS devices running QTS software
TP-Link R600VPN